Most people look at a report that comes from a software system and believe what it says. But not everything is as it seems. As I will explore in this article, data in a database can tell a much different story than the reports the software can print.
Background
First, let’s define a database. Databases are collections of similar data. Generally speaking, databases are digital and allow for the creation, editing, maintenance, searching and reporting (among other functions), of the information contained within the database. A check register is a good example of a database. A standard check register would have columns: Type ( check or deposit ), Check Number, Date, Payee and Amount. Each check would be stored in a row or record in the database. Entries into one’s check register, whether in paper form or in electronic form, would generally be made in chronological order.
Next, let’s examine the function of software. Software that uses a database can generally retrieve specific records from that database and report them in almost any order. So while data may be entered in the wrong order, the software that is retrieving and reporting the information actually filters and sorts the data before displaying it on the screen or sending it to the printer. Going back to our check register example, if some checks were entered in the wrong order, the reporting function of the software has the ability to sort the checks within a certain parameter. For instance, the user can sort by check number, date, amount, or any other sorting function the manufacturer allows the user to choose, regardless of the order in which data was entered.
The Case
This case involves two Arizona companies: The Plaintiff company is a medical billing company that claimed it was owed fees by the Defense. The fees were calculated as a percentage of the revenues received by the Defense for which the Plaintiff did the billing. The Plaintiff also maintained that it performed in accordance with its contract and that it diligently performed its collection duties.
The Defense had contracted with the Plaintiff company to handle their billing. The Defense would package their paper records and deliver them to the Plaintiff for data entry and billing. The Defense filed a counterclaim saying the Plaintiff didn’t perform their duties and that the Plaintiff neglected to diligently collect the fees for client services rendered by the Defense. In the beginning, Evidence Solutions, Inc. (ESI) was hired to perform services for the court, as appointed Special Master. ESI was instructed to determine what information was available from the software system used by the Plaintiff to perform the billing for the Defense. ESI was hired by the court to print reports from the software so that both sides could validate data already disclosed in the case. It seemed to be a reasonable request. Unfortunately, the request became more difficult because the Plaintiff company didn’t have the original software installation media. ESI encountered several problems and could not readily get the software working by simply copying it from the Plaintiff's computer. Evidence Solutions contacted the software manufacturer and attempted to obtain replacement software or information about making the software usable. Looking for alternatives while attempting to get the software working, ESI extracted data from the proprietary database format used by the billing software. The tables were examined to help determine what information might be available in each database. As we searched through several databases and extracted data for examination that appeared to be log or transaction files, we found data that was out of order:
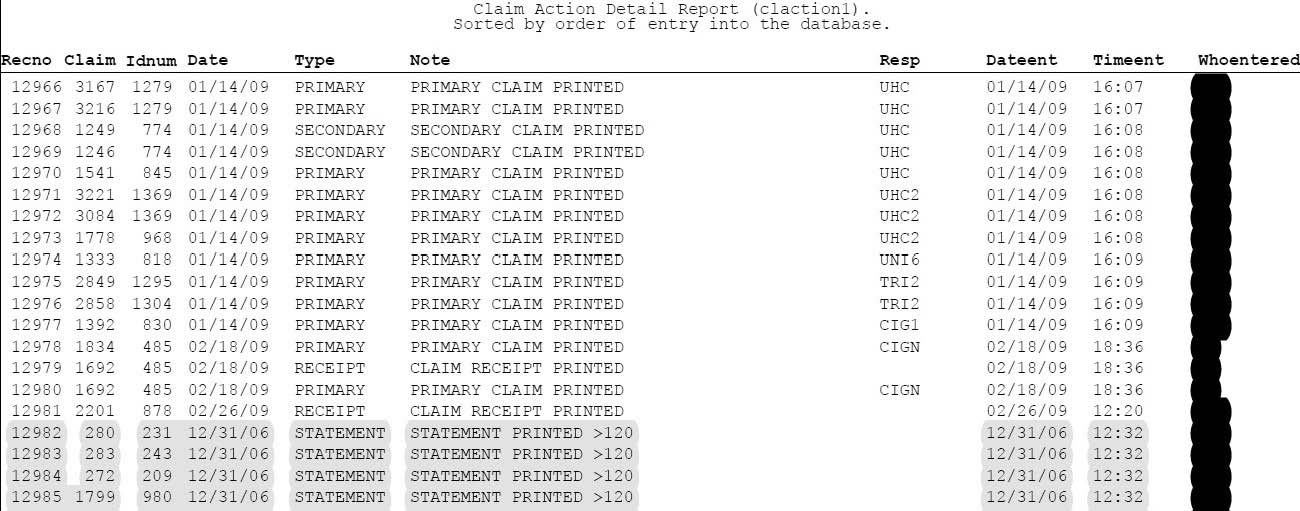
Figure 1
The data in Figure 1 is in the order in which it was entered into the software system. The DATEENT column shows that data was entered out of order. The entries at the bottom of the example show that the date on the computer was 2006 when the data was entered. Since there is data from 2009 immediately above these records, we were able to determine this data was fabricated in 2009. We determined the computer system date was changed to indicate December 31, 2006, just before these statements were printed by the Plaintiff. Not only did the Plaintiff set the date to December 31, 2006, and run statements they also ran statements for each of January 31, 2007, February 28, 2007, and March 31, 2007.
ESI was able to determine that the Plaintiff created over 1900 false records related to the printing of statements. The software would report that statements had been printed for outstanding accounts monthly for a four (4) month period when it was found they had actually been printed on a single day in 2009. The software would list these entries in chronological order on each of the patient’s records. When viewing this information from the software, everything looked normal.
Shortly after the distribution of this data, the court determined that ESI and Scott Greene should be released from Special Master duties. Upon that release, ESI then became an Expert Witness for the Defense.
The Plaintiff’s data manipulation didn’t end with back-dating statements. They selectively created other records. For instance, for Patient ‘A’, the system reports the following entries:
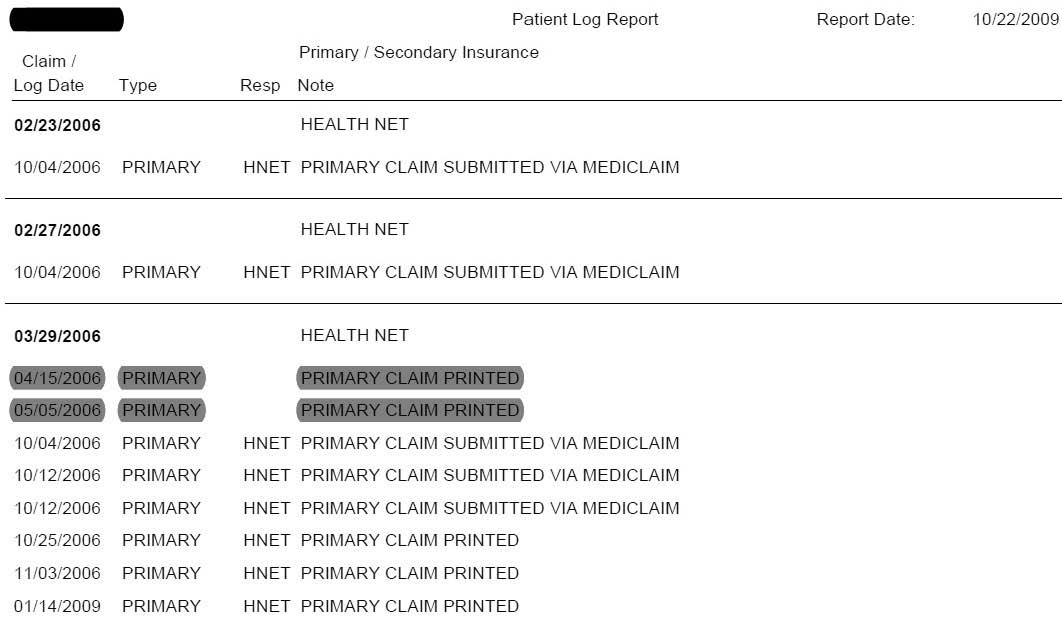
Figure 2
The line items dated: 04/15/2006 & 05/05/2006 are forged entries in the data. The report in Figure 2, due to its coming directly from the software system, displays all of the data in date order. When examining the actual data in the database, however, the data looks much different:
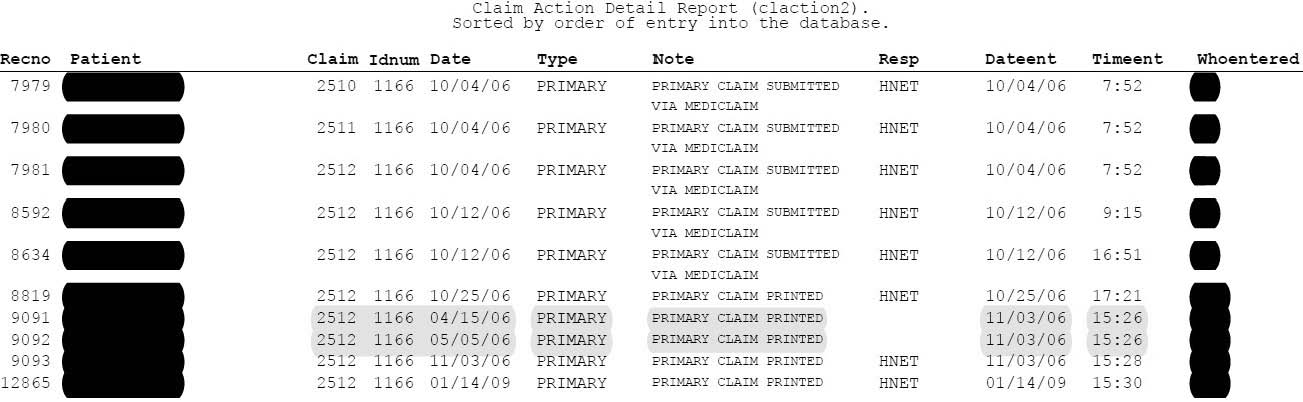
Figure 3
The line items actually are third and fourth from the bottom of the database of entries in Figure 3. They were not created on 04/15/2006 & 05/05/2006 as they appear in Figure 2, instead, they were both created on November 3rd, 2006, several months later than the software report would presume to represent. It then became the Defense's position that most of the forged data was created by the Plaintiffs to bolster the Plaintiff’s position that they had diligently attempted to collect the funds due to the Defendant company.
The attorneys ESI worked with were integral to the discovery of several things in the data. ESI created a custom report sorted by type of claim that listed all of the claims for which there were no payments. Using the same reporting format on the page, the facility fees that had no payments spanned three (3) pages. The professional fees for the same time was more than 8 pages long.
The next issue examined by Evidence Solutions was the amount of activity there was for each type of claim. A custom report was created to evaluate the number of activity items per claim. Each electronic claim submission, bill or statement printing represented a single activity. These were then counted and those with minimal activity were defined as those claims with one or fewer attempts to collect. Again using the same format for each type of fee, facility fees were listed on a single page while professional fees filled three (3) pages. Once the data was compiled ESI was also able to determine just how fast claims were being submitted for payment by the Plaintiff. While the Plaintiff represented that claims were being treated relatively equally, ESI created a report that calculated the number of days between the date of service and the date the data was entered into the system for billing. Facility fee items which were the largest dollar amounts were billed in an average of 18.7 days, the smaller dollar amounts for professional fees averaged 34.3 days.
Based upon the custom report ESI created, a pattern emerged clearly showing large dollar facility fees were pursued. Several different methods were utilized by the plaintiff to pursue facility fees as a higher priority to the professional fees. This was especially evident in the key areas of: the time it took to submit the bill to the insurance carrier or patient as well as how many times the fee was pursued by the plaintiff.
While there were reports in the billing software utilized that allowed for someone to review the number of statements printed, it would have had to be printed, it would have had to be done for each individual patient. This would have created a mountain of reports needing an individual willing to take the time and summarize the information. By ESI creating a custom report, pulling the data together into a single report painted an easier to understand picture. Adding the statistics of averages created something that anyone could understand simply by reading the bottom line. See figure 4.
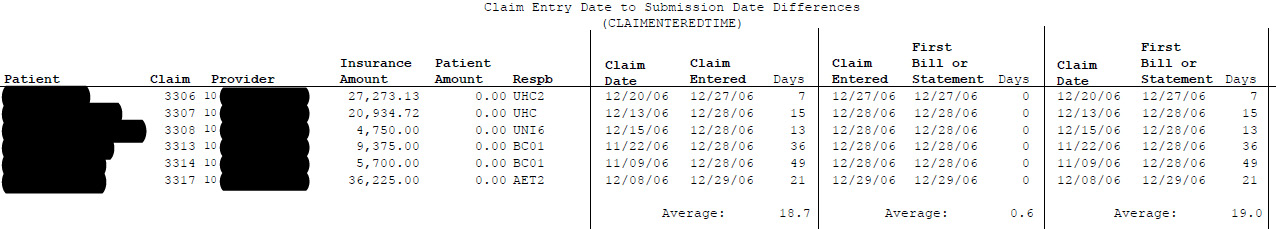
Figure 4
The final report created from the raw data was a report showing each of the payment or credit types for the physician procedures which were not paid. There were two (2) types of writeoffs on professional fees that piqued the interest of the defense attorneys:‘Denied Medical Record Requested’ and ‘Contractual Writeoff’. In less than a year’s time, the Denied Medical Record Requested made up over $90,000. This was odd in that the plaintiff billing company had all of the medical records in their possession when the bills were submitted. They claimed to be well versed in which claims needed copies of the medical record and which claims did not need backup information. The ‘Contractual Writeoff’ category was curious because many of the claims that had little or no activity, and went unpaid by the insurance carriers, were written off using this type of transaction.
The final piece of data, which was not readily available when using the software, is the "Whoentered" field. This field, just like it sounds, records the initials of the user who was logged into the software system when the data was entered. In this particular case, the “Whoentered” was populated with the initials of one person for almost all of the forgeries. The initials happened to match up to one of the company’s owners.
Conclusion
It is important when dealing with data that doesn't seem right, to examine the data in its most basic form. This is usually the database itself. Hiring the right analyst who understands the data, who can create custom reports and help interpret both is critical. Finding an individual or company that understands Medical Billing systems, was critical to the Defense Attorneys who were able to utilize this expertise for their client’s benefit.
In short, evidence that may not appear to exist will suddenly come into focus when you find data has been forged, altered or manipulated.
About the author:
Scott Greene is a Senior Technology Forensics Examiner for Evidence Solutions, Inc. He has been doing Data Recovery, Computer, Technology and Digital Forensics, and EDiscovery work for over 25 years. Scott is the CEO of Evidence Solutions, Inc. Scott and Evidence Solutions have been involved in Civil & Criminal Cases, for Plaintiff, Defense and Special Master in Justice, Superior & District Courts as well as Internationally. He is a frequent speaker for many regional and national organizations. Scott enjoys traveling to share his unique knowledge of technology and forensics.

